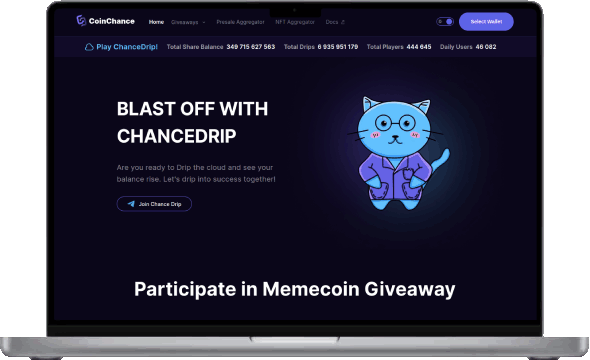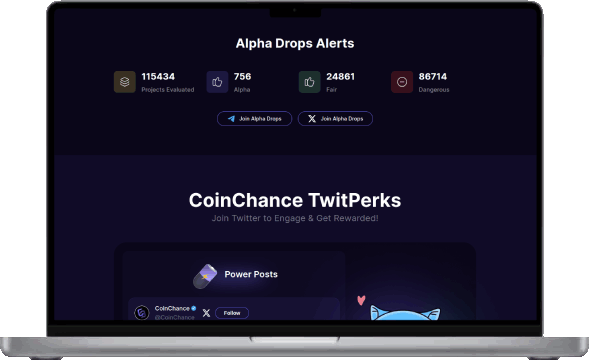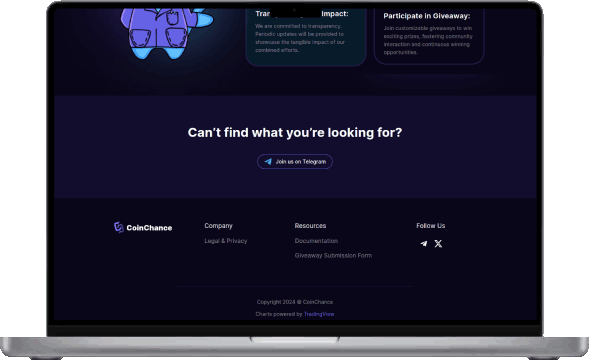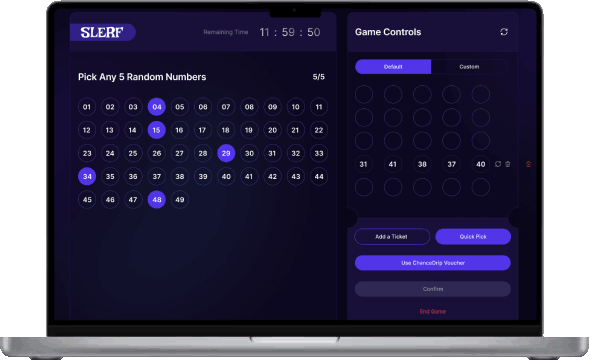
Cyber Security Lab
Our Cybersecurity Services offer proactive measures to identify and mitigate potential risks, ensuring your digital assets remain secure
Quality Genesis IT Lab Delivers



Client Confidentiality



Transparent Data Tracking



Protected Data Management



Secure Data Exchange
Our Cyber Security Solutions Include the following

General Data Protection Regulation

Training on Secure Code Warrior

Cloud Security

Cyber Security Audits

Identity Management

Consultancy
Security Solutions

Software Security Solutions

Tools Development

End-point protection

Cyber Analytics
Tools We Work With

Semgrep

CodeQL

TruffleHog

Snyk-CLI

Yarn-audit

StaticCheck

GoVulncheck

Unified Threat Management

Burp Suite
Portfolio
Process We Follow
Steps Involved in Developing Your Solutions

Reconnaissance
We conduct detailed reconnaissance to detect vulnerabilities and loopholes that attackers could exploit. With this valuable insight, we implement targeted security measures to safeguard your data and strengthen your overall cybersecurity defenses. Trust us to uncover potential weaknesses and protect your valuable assets.

Vulnerability Analysis
We use offensive security expertise, advanced testing tools, and manual techniques to simulate ethical cyberattacks. With a focus on your specific environment and technologies, we conduct thorough tests to identify vulnerabilities. This allows us to provide tailored recommendations and implement robust security measures.

Surveillance
Following comprehensive findings, we prioritize and compile recommendations to guide resource allocation towards areas with the highest potential loss mitigation. By leveraging our surveillance capabilities, we enable informed decision-making and strategic allocation of resources to address identified risks.

Solutions
To verify the effectiveness of our efforts, we conduct thorough penetration testing (pen-testing). This rigorous assessment validates the enhanced security measures, providing assurance that potential attack vectors have been mitigated.
Let's Secure Your Business
Contact our Cyber Security experts today to fortify your defenses.